Another day, another data breach. Every company today must consider Identity Security. From securing employee access to enterprise tools to protecting customers from account takeovers, identity is the new perimeter in cybersecurity.
As AI-driven attacks accelerate – from deepfake-powered fraud to automated credential stuffing – the stakes are only getting higher. Everyone is impacted, from large enterprises like Snowflake to government agencies like the US Treasury, all the way down to mom-and-pop shops with little protection. Even splashy AI model builder DeepSeek was the recent victim of a “large-scale malicious attack.”
CISOs and security leaders face a difficult challenge: managing a vast set of organizational demands – many of which are simultaneously mission-critical. Amidst all the noise, Identity Security has topped the list of CISO priorities two years in a row.
Security teams are scrambling to keep up, but their tools weren’t designed for an era where human and machine identities outnumber employees by orders of magnitude. For startups, this shift presents one of the biggest opportunities in enterprise software. Identity Security has become a top priority for CISOs, and enterprises are actively investing in it, yet the landscape remains fragmented and underpenetrated. Founders who can rethink Identity Security for the modern IT landscape have the potential to build category-defining companies and capture real market share.
Biggest Opportunity in Identity Security
While not a new category by any means, Identity Security has continued to grow as a major threat vector, increasing both the importance of managing identity-related risk and the scope of the identity landscape. AI has also been a major catalyst for identity-related attacks, underpinning everything from sophisticated phishing attacks to deepfake generation.
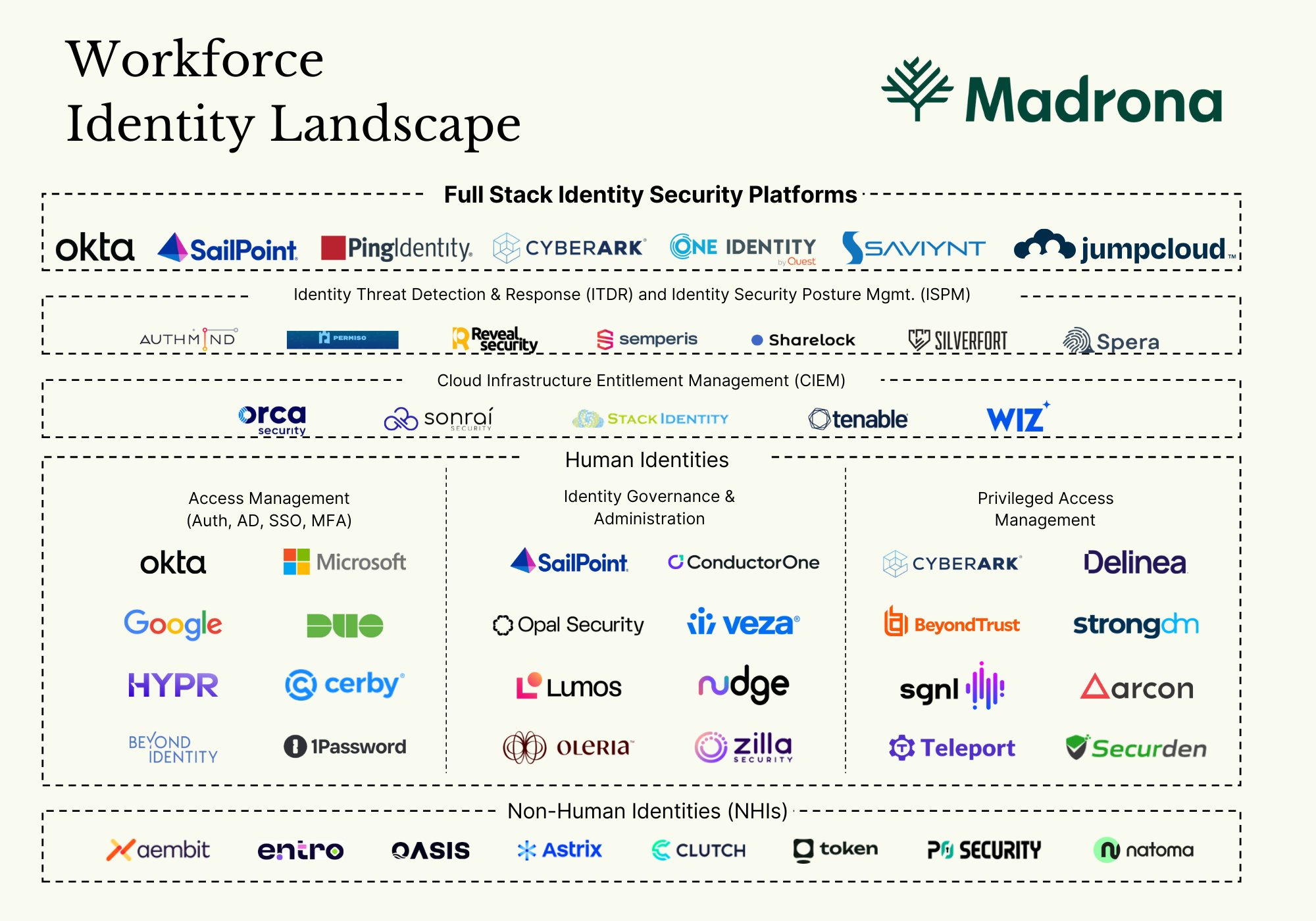
The identity landscape is vast and can be broadly split into two categories: Workforce Identity and Customer Identity. While innovation is happening across both, some of the most pressing challenges today are in Workforce Identity, where enterprises continue to struggle with increasingly complex IT environments that drive downstream consequences.
The foundational components of today’s Workforce Identity infrastructure play critical roles in authentication (who gets in) and authorization (what they can do). These three categories also comprise the largest market opportunities, are experiencing the most consolidation, and are facing competition from next-gen solutions purpose-built for increasingly complex IT infrastructure.
- Access Management (AM): authentication for granting humans real-time access to applications and data
- Identity Governance & Administration (IGA): aggregates and manages digital identities, roles, and access rights
- Privileged Access Management (PAM): authentication and authorization software specifically focused on individuals with greater levels of access
The four remaining key elements in the identity security stack include:
- Non-Human Identities (NHI): Authentication, authorization, lifecycle management, and privileged access for non-humans like SSH keys, API keys, tokens, secrets, etc.
- Identity Security Posture Management (ISPM): Framework to evaluate and strengthen the security posture of identity infrastructure components (i.e., categories 1-4)
- Identity Threat Detection & Response (ITDR): Identification and remediation software for identity-based attacks
- Cloud Infrastructure Entitlement Management (CIEM): Tie into the broader cloud security landscape focused on managing IaaS entitlements
Where Founders Can Build
With so many categories, it’s no surprise customers typically prefer a platform approach over managing distinct best-in-class solutions. In practice, however, this means enterprises often end up implementing multiple platforms or identity providers (IdPs) – leading to visibility gaps, integration challenges, and increased security risks. This is why Identity Security is not a winner-take-all market. Leading companies like Okta, CyberArk, Ping, Delinea, and SailPoint, which is now planning to reenter public markets, have each reached substantial scale ranging from hundreds of millions of ARR to billions in the case of Okta.
Despite the presence of established players, current leaders only capture 10% of the $55B opportunity in workforce identity, according to SailPoint’s estimate. This presents a massive opportunity for startups.
Three main challenges are creating whitespace for innovation: Managing Multi-IdP Environments, Shadow IT and Disconnected Apps, and the Explosion of Non-Human Identities.
Managing Multi-IdP Environments
Enterprise IT environments are a layered cake with components reflecting decisions at different points in the company’s history. Often this is a hybrid environment with IdPs used for only specific components. This creates challenges related to visibility and cohesive management, which IT teams and developers often bear the burden of implementing. This is one dynamic that makes us particularly excited about the value modern IGA solutions like ConductorOne, Veza, and Opal Security can deliver. Remaining agnostic to the underlying IdP breaks down visibility silos, helping drive a more cohesive authorization strategy that simultaneously reduces both identity-related risk and makes life easier for IT teams/developers while creating strategic expansion points into other areas of the Identity stack.
Shadow IT and Disconnected Apps
As many of us were told in childhood, seeing is believing – which makes shadow IT risk particularly difficult to manage. Despite the options for implementing a robust identity stack, non-federated apps (also referred to as disconnected apps) are routinely overlooked. There are a surprising number of disconnected apps – think social media, freemium tier SaaS apps – and half of organizations don’t know how many disconnected apps are in production. Companies like Cerby offer a unique way to modernize disconnected apps and close this gap.
Explosion of Non-Human Identities
Over the past decade or so, another driver of both shadow IT risk and complexity has been the shift to microservices, cloud-native architectures, and DevOps best practices. This has many benefits, to be clear, but has also created a proliferation of service accounts, API keys, and tokens, more recently termed “Non-Human Identities” (NHIs), that present a security risk. NHIs are common in cloud infrastructure environments like AWS, often used in automation workflows like robotic process automation (RPA), and in cross-application communication. They outnumber human identities nearly 50:1.
Part of the NHI challenge is the degree of fragmentation that comes from operating in a distributed ecosystem spanning a variety of services and resources across different environments. Bringing this together in a single architecture is challenging, particularly when the underlying workflows and attributes have some fundamental differences. A few key differences include 1) human-driven vs. automated, 2) least privilege principles vs. overly permissive, and 3) MFA for human identities vs. secrets for NHIs.
The scale of NHIs and challenges posed by a fragmented landscape, we believe, requires dedicated functionality and creates significant opportunities for Founders to solve real customer pain points. Many of these pain points are analogous to different components of the human Identity stack – visibility, lifecycle management, posture management, and detection/response. While NHI companies have selected initial wedges, for example Astrix’s and Entro’s initial focus on inventory and visibility, most NHI companies are quickly evolving to become end-to-end platforms. Notably, some companies like P0 Security aim to serve both human and non-human identities, finding overlap with a developer-centric approach.
Conclusion
Whether evolving to meet the realities of modern IT environments or protect against novel AI attack strategies, one thing remains clear – Identity Security will continue to be an important and ever-evolving category.
What are we missing? Tell us what you think. Whether you are building in identity specifically or elsewhere in the security ecosystem, we’d love to meet. Madrona is actively investing in security and we’ve partnered with next-gen companies like Clerk, Stacklok, Cohesity, Tigera, ExtraHop and several unannounced companies. You can reach out to us directly at: [email protected] and [email protected].